Cybersecurity Technologies Safeguarding Against Potential Threats

“It takes 20 years to build a reputation and a few minutes of cyber-incidents to ruin it”
- Stephane Nappo
(Head Information Security for Société Générale International)
Did you know?
The year 2021 saw an average of $787,671 lost per hour due to the data breaches.
Doesn’t it tell a scary story
That’s how easy it is to scam people and steal their money. which is why it is vital to be aware of these online scams so that you can further protect yourself.
While there are many benefits to innovative tech, the downside is that there’s simultaneous advancement in cybersecurity risks, too. As security is a key consideration of any business,
So in this read we will explore cybersecurity technologies to safeguard against potential threats.
Let’s start.
Random Number Generators
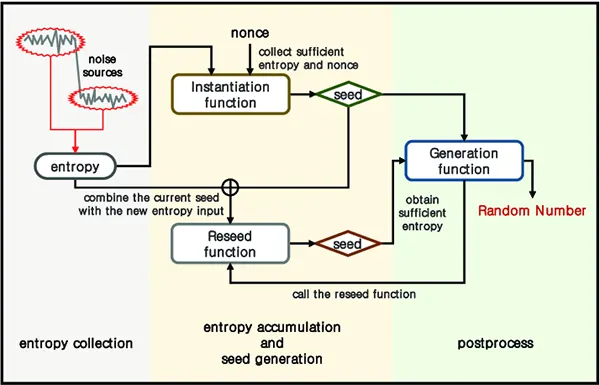
Random number generators (RNGs) have long since been used in a wide range of industries to digitize the element of chance. Essentially, It mimics the same luck as rolling a dice, choosing a card, or spinning a wheel. For this reason, you’ll commonly see them used in online casino games – especially slot games.
For example, when you play Big Racing at Paddy Power RNGs are used to determine which symbols land on the reels when, ensuring that results cannot be predetermined. This is also used for a virtual horserace, providing players with gameplay that is immersive, authentic, and fair.
This same technology can be utilized in business settings to enhance security for employees, consumers, and other stakeholders alike. It can be integrated into a comprehensive password policy, suggesting unique and unrelated passwords made up of a randomly generated sequence of characters.
Encryption software will have integrated RNGs to protect sensitive data. They can also be used in conjunction with payment security systems to tokenize sensitive card data between the point of sale device and the consumers’ bank. This provides an extra layer of protectio nto a wide range of applications and industries.
Multi-Factor Authentication

Put simply, multi-factor authentication (MFA) is a protection layer that requires people to use multiple independent verification processes before they can log in or complete a transaction.
According to TechTarget, there are several different methods that can be used in combination with one another depending on the application. Just some examples of verification include passwords, one-time codes, personal identification numbers (PINs), security tokens, or even biometric methods.
Perhaps the most common type is two-factor authentication (2FA), which only requires a secondary method. Though this might be ample for low-stake settings, those who require additional levels of shield can build a robust MFA that reflects their risk of threat.
If a business deals with several levels of protection within diverse teams, an adaptive one is an option that chooses a different verification method depending on the context. It is said that an effective solution can reduce safety breaches by up to 99% compared to just passwords.
Did You Know?
Cybersecurity statistics indicate that there are 2,200 cyber attacks per day.
Network Protection
In the age of remote and hybrid working, it is estimated that 32.6 million Americans will work remotely by 2025. This comes from research by Upwork, as reported by Forbes, suggesting 22% of the population will be based from home. With this in mind, it is important to ensure you have the same level of web protection for isolated workers as you would in a physical office space.
A virtual private network (VPN) encrypts data that is transmitted through the internet, creating a secure connection between those who work from home and their head office.
This allows remote workers to connect to the internal web securely through their home devices. Firewalls are also key for both distant and in-office employees, as they monitor traffic on the web and restrict access to unauthorized personnel.
As you can see, cybersecurity technologies are essential for any business in any industry. With these examples in mind, take a look at the different solutions out there to find which security methods work best for you.
Also…
On average there is one cyber attack is happening in every 39 seconds.
Final Thoughts
In closing, Safeguarding yourself from cyber threats is vital for your data, money, and other valuable assets. There are several ways you can protect yourself from cyber-attacks such as encryption methods, two-factor authentication, using a private and secured network, and most importantly investing in a cybersecurity expert, it might seem a little expensive at first but it’s worth every single penny, because as Richard Clark says:
“If you spend more on coffee than on IT security, you’ll be hacked. What’s more, you deserve to be hacked”
- Richard Clark
(American national security expert)
How to protect yourself from cyber-attacks?
Following are the 5 easy ways to protect yourself from cyber attacks:
- Avoid using easy passwords like 123456, qwerty, abcdef, and password
- Check the strength of your password
- Check if you have already data breached
- Don’t share your valuable data with anyone
- Secure your device
What are the 5 main threats to cyber security?
Here are the 5 main threats to cyber security:
- Weak Passwords
- Poor Patch Management.
- Ransomware And Malware.
- Phishing And Social Engineering.
- Insider Threats.